The Wall Street Journal reports today: “Hackers in Europe and China successfully broke into computers at nearly 2,500 companies and government agencies over the last 18 months in a coordinated global attack that exposed vast amounts of personal and corporate secrets to theft, according to a computer-security company that discovered the breach.”
The Wall Street Journal reports today: “Hackers in Europe and China successfully broke into computers at nearly 2,500 companies and government agencies over the last 18 months in a coordinated global attack that exposed vast amounts of personal and corporate secrets to theft, according to a computer-security company that discovered the breach.”
This is apparently not related to the attacks from China that caused Google to make noises last month about closing its operations in that country. In fact, the New York Times calmly notes that this is a relatively small blip in the world of compromised computers and botnets. The Conficker botnet reached its peak at 15 million computers and continues to contaminate more than 7 million systems globally. That’s just one of 5,900 separate botnets monitored by one security organization contacted by the Times.
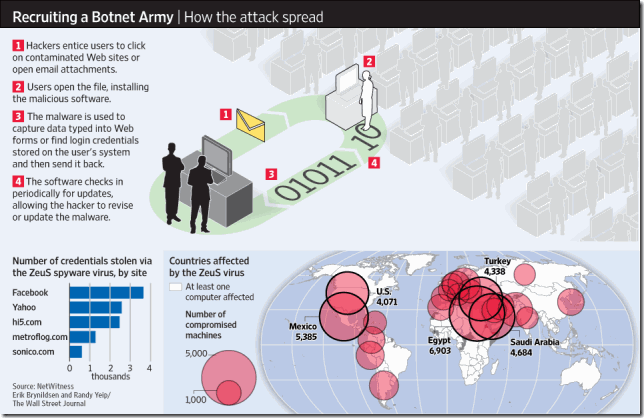
Today’s article describes attacks using the same social engineering that has been prevalent for the last year or two: enticing people to click on contaminated Web sites, email attachments, and ads purporting to clean up viruses. The malware installed by these botnets is designed to evade antivirus software (which understandably relaxes when you click “OK”), and allows your computer to be used for anything from sending email spam to trapping and transmitting your login information and documents. The malware installed by the botnet covered today apparently focused on gathering login credentials to online financial systems, social networking sites and e-mail systems and sending the information back to the bad guys, who then used that information to break into corporate servers and look for intellectual property, credit card databases, and more.
Please be safe out there! Read the rules for safe computing and click carefully! I have dealt with too many compromised computers lately, and I haven’t been able to save all of them. All of the rules are important but I want you to be particularly alert for the most prevalent form of poisoned web site, the phony security warning that pops up and claims that your computer has a virus and asks permission to clean it off.
Know the name of your antivirus software. If you get a security warning that does not display the exact name of your security software, it is phony; if you click on anything, you will probably install malware.
Antivirus software & UAC will not always protect you against malware if you click OK at the wrong time. The bad guys are liars. They will say anything to get past your defenses, without conscience or remorse. Use your common sense. Read and think before you click OK.
If a web site brings something up on your screen that might be malware, do not click on anything. If you click “NO” or “CANCEL,” there is a good chance that they lied and you actually gave permission to install the malware. Turn off your computer (push the power button and hold it in for 8-10 seconds) if you can’t get the malware screen to disappear any other way.