
Windows 7 and 8 are hard to attack if the user does not have local administrator privileges. Small businesses can reduce the amount of adware and malware and cruddy software on office computers by removing administrator rights from employees.
This requires some background, and it’s not a magic bullet – there are some tradeoffs when you implement this. I’m starting to feel it’s an important security measure for many small businesses.
Let’s talk about “administrators.”
A small business with a server knows that there is an “administrator.” The domain administrator is an all-powerful god. All office computers respect the domain administrator. Nothing can stand in the way of the awesome powers of the domain administrator. He or she can install programs on the server, change passwords, grant or deny access to folders, and more. When I get on your server, I log in as the domain administrator with great power. (And, well, you know – great responsibility).
That’s not the only kind of “administrator.”
Each computer – every desktop computer, every laptop – also has local administrators. A local administrator also has unfettered power, but only on that individual computer.
By default and by common practice, every user is given local administrator privileges. When your employees log into their office computers, they are local administrators. When you log into your notebook, you are a local administrator. When the domain administrator logs into an office computer, he or she has local administrator privileges because the server controls security and grants local admin privileges to the domain administrator on all domain computers.
The important part of being a local administrator is that you can install programs on the computer without asking anyone’s permission.
When you log in as a local administrator, you are given a magic token. As long as they are holding the token, nothing will stop an employee from installing a “free” game or a “free” PDF converter or a “free” media player along with some adware and viruses. Under some conditions, your programs inherit your magic powers and the bad guys can use them to, say, install Cryptolocker from a poisoned website without even presenting a UAC prompt.
That’s not all. As a local administrator you have the power to do anything to your computer, including the power to destroy it. You can go into system folders and delete files needed to keep the computer running. You can edit the registry and kill the computer in seconds. You can reformat the hard drive. You can delete user accounts. At worst, you’ll get a UAC prompt, the OK box that greys the screen and asks if you’re sure you know what you’re doing. You’ll ignore it and click OK and the computer will do what you asked.
The alternative is a standard user account. A standard user can use programs and change settings that do not affect the security of the computer – change wallpaper and choose a default browser and save Internet favorites, say. But a standard user cannot install programs or take any other steps that bring up a UAC prompt – setting up a printer, for example.
When standard users try to do something that they do not have permission to do, the computer requests the credentials for an account that has local admin privileges.
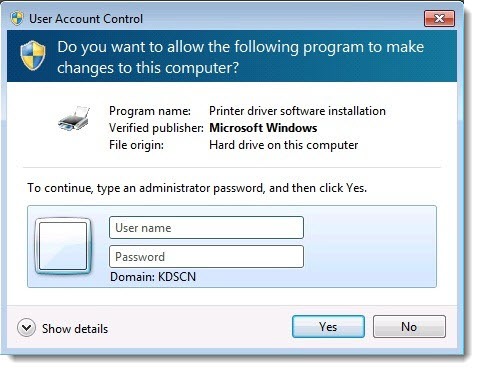
Medium size businesses and enterprises have locked down employee computers for years. If you work for a big company, you don’t expect to be able to install new programs. The above prompt can only be filled in by calling the IT helpdesk and justifying what you want to do. It’s standard practice.
The constant spread of adware and malware is increasing the need to spread that security protection to small business employees. A few years ago, one typical report concluded that most Windows and Internet Explorer vulnerabilities simply disappear when local admin privileges are taken away from users.
Small businesses don’t have an in-house IT department and employees should not have to wait for my callback to install a printer driver. There is usually one or two people at each business – the owner or office manager, say – who are almost always there. I make those people local administrators on the employee computers. When the above prompt comes up, the employee has to bring the office manager over to the computer so the credentials can be filled in. It gives the office manager a chance to discover whether the employee is doing something that seems like a good idea (or perhaps consult me about it).
There are only a couple of downsides, but they’re meaningful.
• Employees hate this at first. The policy needs to be clearly explained and presented without apology.
• The office manager or other onsite person with the magic credentials has to be trained about what to expect.
• More importantly, this only provides protection if the office manager does not let other people know his or her password! If employees can fill in the office manager’s name and password, this merely adds annoyance without adding any security benefit.
• If there is a short-tempered Great Person in the office – the owner, the senior partner – perhaps they should be left out of this process. At 11:58am a Great Person who cannot install a WebEx plugin for the noon meeting might draw, shall we say, the wrong conclusion about how valuable this is.
I’m going to be discussing this with many of my clients, especially the ones whose employees have demonstrated a lack of restraint about downloading online crap to pass the time.


Mike,
Do you want cryptolocker? Because that’s how you get cryptolocker.
The difficulty is, as Mike says, administration of endpoints and empowerment of the users.
The solution is least privilege using a privilege management tool. You give the user the least privilege that they need to do their job while giving only the programs that require elevation admin rights. This works using a predefined white list of apps.
Thus only the apps you know run with admin rights, mitigating most of the risk.
No one should operate a computer as an Admin. But no one should be denied an admin password.
The employees who stay after you take away local admin are the ones you probably don’t want to keep.
Your employees ability to innovate and learn new software to apply to their jobs requires Admin. No innovator is going to wait for a manager or IT admin to approve their installs.
Good luck backing up the os without local admin.
Whatever happened to empowering employees?
If you are a cash cow, then go for it.
If you want to grow and flourish, forget it.
Don’t your employees have Admin rights on their personal computers?
Why don’t you try taking those away too?
Treat employees like they can’t be trusted, and you’ll be right.
unfair , I need way to break that to be able to install programs plus I can not see administrator log in