Let’s start with two familiar security principles.
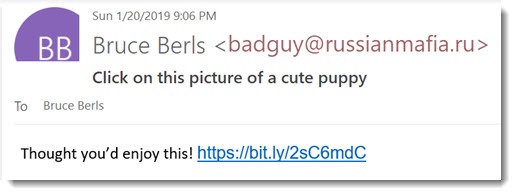
• The bad guys can make any name appear as the sender of a malicious email message.
• Frequently the email address does not match the name. It’s one of the indicators that a message is fake.
The screenshot above is an example. You should always look at the email address of the sender before you click on anything in an email message. There are a thousand variations on malicious messages! The bad guys may pretend to be a client or a friend with a link to click on. They may pretend to be FedEx with a package to deliver, or Dropbox with a shared file for you, or Microsoft with a notice that your mail is about to be turned off. The real goal is to install a virus or more often to convince you to type in a password that they will use to hack your mailbox or your bank account.
Now let’s add one more trick that the bad guys are starting to use more frequently.
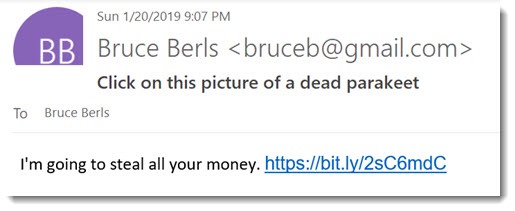
• The bad guys can make the sender’s name and email address appear any way they choose on a malicious message.
The screenshot above is an example. There is no easy way to tell that it came from the bad guys instead of my Gmail account. (These are hypothetical examples that I mocked up in Photoshop, but you get the idea, right?)
Apparently there’s nothing new about this trick, but until recently I rarely saw a spoofed email address. The sender’s name would appear to be familiar – Microsoft or FedEx or someone from our address book – but the email address would be an obvious giveaway. In the last couple of months, I’ve seen several messages to clients with the name and email address of known senders who had not sent the messages.
Technically it’s slightly more difficult for the bad guys to fake the email address, but now the bad guys are going to the extra trouble. When a message comes in with the name and email address of someone you know, it takes extra paranoia to continue to be suspicious of the link in it to what purports to be a Dropbox file or a cute picture of a dancing uvula or whatever it claims to be.
Pro tip
Under the hood, an email message has two different places to store the sender’s email address. One of them appears in Outlook and other email programs – the FROM: header. That’s what the bad guys are manipulating; it’s not checked against the domain SPF record.
If you look at the message source, the other is the MAILFROM: header (aka the “envelope sender”), used for a slightly different purpose behind the scenes. There is also a REPLY-TO header which may not match the FROM: header. Both of those might contain clues to the true source of the message, but neither is readily available to the end user. The sender’s IP address can also be examined to see if the message came from some exotic country filled with cybercriminals. This Microsoft TechNet article has a good explanation of how to troubleshoot and identify spoofing attacks.
What you can do to be safe

• Look at the email address of the sender before you click on anything in an email message. If it doesn’t seem to match what you expect, it’s probably a fake.
• If the name and email address match, think about whether the message makes sense. If it’s something you don’t expect, assume it’s poison and try to talk yourself out of it before you click on anything.
• If the sender appears to be someone you know, don’t relax. The bad guys assemble their mailing lists from social media, from company websites, and from hacked address books. Maybe you and your friend have never been hacked, but your names are both in the address books of someone who really was hacked. Eventually the bad guys will put together messages from one of you to the other, just in case you know each other and they can get past your guard.
• If you click Reply, make sure the email address you’re sending to matches what you expect. There are several ways the bad guys can create their spoofed messages. In some of them, the Reply message goes to a different address than the one shown as the sender. It might be a clue that there is evil afoot.
Just because the sender’s name and email address appear on an incoming malicious message, it does NOT necessarily mean that the sender’s mailbox has been hacked
This is the most interesting part of this for IT professionals. The first time a client got a malicious message with the sender’s name and email address of someone in the company, I assumed the sender’s mailbox was hacked. Message traces in Office 365, though, made it clear the message had not come through the user’s mailbox. It wasn’t until I researched it that I discovered this bad guy trick, and where to look in the message source for evidence.
If someone notifies you that they received a malicious message from you, paranoia should lead you to change the password and make sure you’re in control of the mailbox right away. Sometimes your mailbox will really be hacked! But not always.
If you haven’t been hacked, there is literally nothing you can do if someone is using your name or email address to send out spam.
Be careful out there!

Trackbacks/Pingbacks