 The technical side of Google’s blowup in China is shaping up as an explosive story about technology and hacking. Keep an eye on this one!
The technical side of Google’s blowup in China is shaping up as an explosive story about technology and hacking. Keep an eye on this one!
On Tuesday Google announced that it would no longer comply with Chinese censorship demands and might cease operating in China altogether. As I understand it, Google has set up a separate search page that operates within China and censors some search results as requested by the Chinese government. I believe Google also cooperates with the government in blocking access to Google.com. Update: Apparently Google.com can be reached from Chinese computers but search results are censored. It’s unclear whether that’s done with or without Google’s help.
The initial reaction focused on Google’s decision to stop censoring search results. Free speech and civil liberties advocates hailed Google’s decision and looked forward to the additional pressure this would place on the Chinese government.
The underlying story, though, turns out to be far more than a decision made by Google out of good will and high moral standards.
Around Christmas, a number of cyber attacks were going forward:
- Attacks against Google and more than thirty other large companies, seeking to steal intellectual property – presumably valuable bits of software and code.
- Attacks seeking access to the Gmail accounts of Chinese human rights activists. Google’s description suggests that this was a goal of the same attackers that targeted the large companies.
- Independent attacks on the email accounts of dozens of Chinese human rights activists.
Google counterattacked and hacked into the attacking servers (located in Taiwan, Texas, and Illinois) and found some evidence that the attacks were sponsored by the Chinese government or proceeded with the knowledge and cooperation of the Chinese government. Unfortunately the servers were shut down before Google could discover conclusive evidence implicating the Chinese government, leaving the US government in an impossible position, since it has not been given any conclusive technical grounds for accusations or action against the Chinese government.
Adobe has acknowledged being targeted, and the Washington Post reported that other targets were Yahoo, Symantec, Northrop Grumman, and Dow Chemical. One Verisign report said the attacks have some of the same characteristics of attacks disclosed in July, leading to the possibility that in fact this has been an ongoing campaign of industrial espionage against US companies for more than six months.
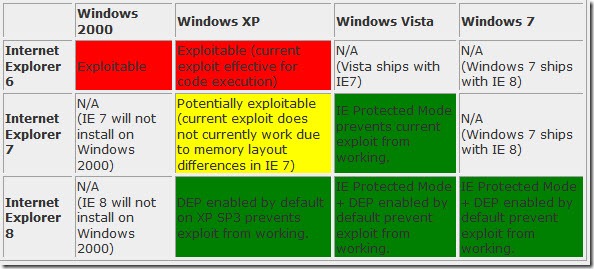
Microsoft acknowledged that a security hole in Internet Explorer played some role in the attacks; technically the vulnerability exists in several versions of Internet Explorer but it only version 6 that was exploited in the wild and versions 7 and 8 are far less likely to be affected. In any case, it seems the exploit requires that a user be fooled into clicking on something dangerous, so the primary vulnerability continues to be a lack of common sense and safety awareness. McAfee has a nice blog post about the technical details of the malware. (Microsoft also said it has no plans to stop operating in China.)
Update: for all intents and purposes, this vulnerability can only be exploited in Internet Explorer 6 running on Windows XP. Here’s a chart from Microsoft Security Research showing where the hack can be exploited:
All the attention has been directed to Google’s decision about censorship and the attacks on mail accounts of human rights activists. Those might both be a distraction from the real story, which is one of two things:
- The Chinese government has actively sponsored the largest cyberattack in history, aimed at stealing intellectual property from more than thirty of the largest companies in the world. Some of the attacks were aimed at companies with defense contracts, although apparently not directly at our government servers. This could become a national security issue that will shape policy for years to come.
- Or: Google’s servers and the servers of other companies were taken down by Chinese hackers because our computing technology does not yet deserve our respect and our confidence. In that case, Google is raising the specter of Chinese government involvement as a distraction to keep us from realizing that the cloud is not yet a secure place for our sensitive data. Here’s Douglas Rushkoff speculating about that possibility.
Update: Don’t be distracted by the attention paid to Chinese dissidents and human rights activists. I think the real story is in Google’s official Enterprise blog:
This was not an assault on cloud computing. It was an attack on the technology infrastructure of major corporations in sectors as diverse as finance, technology, media, and chemical. The route the attackers used was malicious software used to infect personal computers. Any computer connected to the Internet can fall victim to such attacks. While some intellectual property on our corporate network was compromised, we believe our customer cloud-based data remains secure.
Hackers did not launch attacks on Northrop Grumman looking for dissident emails. Google admits that some intellectual property was actually stolen. There is much more to be learned about this side of the story. When you see something like: “This was not an assault on cloud computing,” you should be hearing: Pay no attention to the Chinese hackers behind the curtain. These are not the droids you’re looking for…”
We’re just at the beginning of this one. The US State Department will be asking China for official explanations soon. Watch for more developments!


Trackbacks/Pingbacks