
Passwords are the keys to your digital kingdom. Everything important on your computers and online is secured by passwords. Your passwords are your defense against identity theft, financial loss, compromised computers, and breaches of confidentiality and privilege. If you use a weak password, or if you use the same password over and over every time something calls for one, you are jeopardizing yourself and your business.
The basic rules of passwords are easy to list, harder to put into practice.
— Use complex passwords. (Pro tip: use a phrase. Most passwords can include spaces now. If your password has several words with spaces and a typographical character – “Honky Tonk Women!” – it will not be cracked.)
— Don’t use the same password at multiple sites.
As we discussed last week, it’s more important than ever to use LastPass or another password manager to keep track of your passwords securely.
There are two more simple but crucially important things you can do to improve the security of your passwords.
(1) If you are asked to type in a password hint as part of the process of setting up an account, never ever type something that would allow the password to be guessed. Don’t try to be clever. If you need that hint to remember a password, then you’ve chosen a weak password; you don’t need a hint, you need a better system to manage your passwords. The best password hint: “Look in LastPass.”
(2) Many online accounts include a security question that is used to authenticate you if your password needs to be reset. The answer does not have to match the question. Think of something that you will use as your security answer going forward – words that you will remember but that no one will guess that you chose. Use those words to answer security questions consistently, with the same capitalization and spelling every time. First pet? “Inigo Montoya”. Mother’s maiden name? “Inigo Montoya”. Street you grew up on? “Inigo Montoya”. Elementary school? “Inigo Montoya”.
No one is fact-checking those answers. When you call in to reset your password, the tech support rep types in what you say to see if it matches. The rep doesn’t care if it makes sense. The only crucial thing is that you have to remember what you chose. Make a note of it in LastPass!
ADOBE’S PASSWORD DISASTER
More details are coming to light about Adobe’s catastrophic security breach last month, which I wrote about here. Adobe’s original announcement was that hackers had downloaded email addresses and passwords for three million Adobe accounts, along with a significant breach of credit card data. A couple of weeks later, the company revised the estimates and said that 38 million accounts had been compromised.
It was worse than that.
The stolen database has now gone online for hackers worldwide to look through at leisure – and there are 150 million records in it.
It’s approaching world record territory as one of the largest security breaches in history, at least in terms of the number of people potentially affected.
(Adobe claims that the database includes inactive accounts and “only” 38 million records belong to active users.)
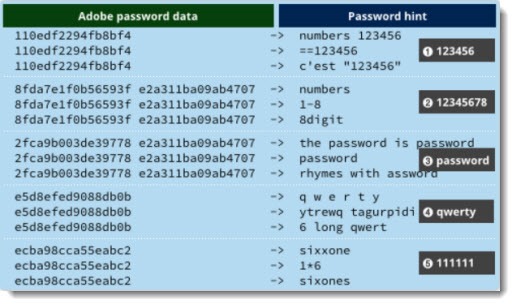
The scary part concerns the passwords for Adobe accounts. Researchers at Sophos Labs published a lengthy analysis of the password data in the stolen database. It’s technical but it’s fascinating reading – and a scary lesson in why it’s important not to give away your password in a poorly chosen password hint.
The email addresses are stored in the database in plain text. The passwords are strings that look like encrypted gibberish to the naked eye. The trained eyes at Sophos (and smart bad guys) have figured out that the encryption was done in a weak way that preserves lots of clues about the underlying passwords. The most telling clue is that the same password is always encrypted into the same string of characters. Unraveling one string opens the accounts of everyone who uses the same password.
But the truly unforgiveable part is that Adobe stored the password hint in plain text along with the email address.
When the Sophos researchers were done cleaning up the data, they were able to produce a crib sheet like this very easily.
If they can do it, the bad guys can too.
As Sophos puts it: “With very little effort, we have already recovered an awful lot of information about the breached passwords, including: identifying the top five passwords precisely, plus the 2.75% of users who chose them; and determining the exact password length of nearly one third of the database.”
Take your passwords seriously, but don’t panic about this Adobe breach. There are a couple of mitigating facts.
According to Adobe, the stolen credit card data was stored separately and was more deeply encrypted. The hackers stole credit card data on three million accounts but to date there have not been any reports of compromised credit cards from this breach.
As to the passwords, Adobe (weakly) defends itself by saying that for a year it has been using a better encryption scheme for protecting its primary password database. The stolen data came from a backup system that was due to be decommissioned. (All Adobe passwords have been reset since the breach.)
Don’t type in password hints that would allow your passwords to be guessed. Don’t answer security questions directly. And be careful out there!


Trackbacks/Pingbacks