The hacking attack against Sony Pictures might be the most significant corporate intrusion in history – and the first salvo in a new and dangerous escalation of cyberattacks against governments and businesses.
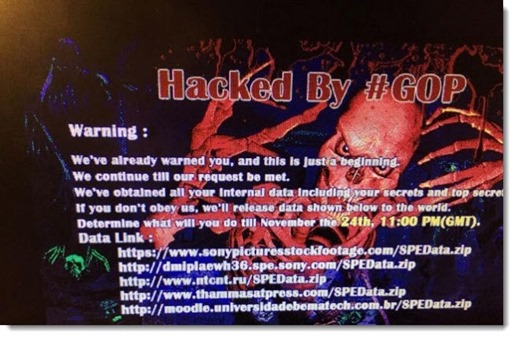
On the Monday before Thanksgiving, Sony Pictures’ employees – all of them – discovered that their Windows computers were unusable, displaying the threatening image above. At the same time, Sony websites were taken over and hacker messages were posted on Sony’s official Twitter accounts. The company immediately locked down its entire network and took its email and messaging systems offline. At the same time, it went into PR containment mode, so details have been scarce about what has been happening.
All of the evidence that has emerged since then has been scary. For a week most employees had to do their work completely without office computers, using phone calls, handwritten notes and fax machines, or working from home and using personal email accounts. There are reports that some employee computers are not being cleaned – they’re being completely replaced with new equipment.
The hackers claim to have stolen huge troves of corporate information and data, and have been proving it by releasing movie budgets, extensive (and highly confidential) information about employee salaries and bonuses, social security numbers, health care files, unreleased films, and all the documents with the word “Password” in the title – spreadsheets and Word docs with keys to Sony computers and servers as well as YouTube accounts and more.
Apparently at least some computers were hit with a virus that completely wiped the data on them. The virus is so dangerous that the FBI issued a warning about it to other businesses this week that did not identify Sony but clearly was a response to the Sony hack.
This attack required careful preparation and could not have been executed quickly. Sony may not admit it but the bad guys could only have done this by penetrating the network some time ago, extensively mapping the company’s global network architecture, and laying traps – creating accounts with admin privileges, leaving back doors into critical systems, following trails to learn more administrator level passwords, and planting viruses that avoided detection until the time came to launch the attack.
It’s serious stuff. Hacked credit card info (Target, Home Depot, Staples) is inconvenient and can cost a business quite a lot in expenses and harm to its reputation, but the Sony attack paralyzed a major global company for a week, which takes it to a much different threat level.
If you want a chilling look at where the world is headed, look at the report released this week claiming that Iran has been successfully hacking into US government and business networks for two years, including commercial airline carriers; suppliers responsible for aircraft maintenance, cargo and refueling; chemical and energy companies; defense contractors; universities; and transportation providers. Imagine that a Sony-style attack is launched to bring down energy companies or an airline.
More of these attacks have been going on than you realized. Three major South Korean banks and two of the largest South Korean broadcasters were attacked last year and suffered serious disruptions. In 2012 data was erased from thousands of computers at Saudi Arabia’s national oil company, taking down the company network for a week. There are constant reports of attacks against America government agencies and companies.
The reporting on the Sony attack has focused primarily on speculation that it was sponsored by North Korea, perhaps to show displeasure about the upcoming Seth Rogen movie poking fun at North Korea. Maybe that’s true. It certainly fits all our stereotypes about North Korea, and there is credible circumstantial evidence supporting that possibility. At the moment, though, it’s all speculation by reporters who are starved for information – not a great atmosphere for accuracy and thoughtful reporting.
If you want an entertaining way to get a glimpse at what the world is like behind the scenes in the work of network security, read the Jeff Aiken novels by Mark Russinovich – Zero Day, Trojan Horse, and Rogue Code. Mark Russinovich is a Microsoft Fellow and generally agreed to be Really, Really Smart. The cyberthrillers show a security expert tracking down hacking attacks on utilities, airplanes in flight, the stock exchange, and the U.N., and probably are uncomfortably close to the truth about what’s going on out of our view. No worries – there are also a lot of people shooting guns and running around to make the stories fun to read.
Keep an eye on the reporting about the Sony hack. It may be a harbinger of more destructive attacks to come.

Trackbacks/Pingbacks