Educate.
Encourage.
Enforce.
It’s all about security. That’s today’s job for a small business IT consultant.
There’s been a consistent curve to technology adoption over the years: enterprises build their businesses around giant-sized technology-based processes, then similar, simplified versions of the same technology are made available to small businesses. Large businesses set up rooms full of servers in the 80s and 90s, then Microsoft Small Business Server brought some of the same services to ten-employee companies. Enterprises set up Exchange Server for 100,000 employees, then years passed and now even the smallest business has Office 365 mailboxes.
Now I’m seeing the bad guys following the same curve – even very small companies are facing targeted attacks by criminal hacking groups. That’s where a bad guy hacks into your mailbox after you get an email from “0fffise 3665 Voicemailery” and click on the link and fill in your password because who knows, you’ve never gotten voicemail recordings before but maybe that’s something new, right? The bad guy takes time to learn about your company, your mail, your finances, sets up a couple of rules in your mailbox to divert incoming replies about the scam, copies your signature. Then an email is sent to one of your customers asking for payment of an outstanding invoice, but it requests payment by wire transfer to an account at Bank of Ukraine. Or maybe it’s an email to one of your employees asking for a wire transfer – and the bad guys know you’re out of town because they’re watching your Facebook feed, and the email looks like it comes from you because they registered a look-alike domain name to fool your bookkeeper. I’ve heard several stories involving follow-up phone calls to the customer by the bad guys demanding payment ASAP. Phone calls!
The security practices used by big companies have been out of reach for small businesses, undoable without an in-house IT department. That’s what I see changing now. Microsoft and other companies have been preparing for this onslaught for years and the tools used by the big kids can now be implemented by small business IT consultants if they’re young and their brains aren’t yet full, both of which are reasons that it’s time for me to step off the train.
In the world of very small businesses, money is always tight and a few strong personalities make all the decisions. If there’s any one thing you can do for your clients, it’s whatever is necessary to convince them – or force them – to use two-factor authentication. It’s a hard project to sell. From the consultant’s perspective, it’s hard to monetize. You can force 2FA for Office 365 with a couple of checkmarks. It doesn’t require much training, just some time to deal with the inevitable hiccups. There’s no immediate reward for the users – it’s not like some business process is improved. But the additional security from 2FA is priceless.
That’s the role for education about why security is necessary, and nonstop encouragement to get everyone through the learning curve for whatever new security process is imposed. You need the users to be converts to the 2FA religion because much of their exposure is out of your control. You can force them to use 2FA for Office 365 and perhaps one or two other business services, but what you really want is for them to become True Believers and secure their personal accounts, lock up their Google accounts, use 2FA everywhere, stop using the same password over and over, and use a password manager.
Education and encouragement – but that’s only the beginning.
There are some simple projects to lock things down for small businesses, but I wasn’t always diligent about them. How about you?
Infrastructure ages out. Routers are far different today than they were five or eight years ago. A sixty dollar Linksys router was good enough for a tiny office back then. Any of those still in service? It’s up to you to convince that client to upgrade to an enterprise-class router. The offices that set up their own equipment to save a buck – anyone still using the default login and password for their network equipment? They’d better not be doing that on your watch. You have to save them from themselves.
Another simple project, a bit of billable time: have you set up SPF, DKIM, and DMARC records for your client mail systems? It’s easy once you know how to do it. I think. I’m not sure because I’ve been procrastinating and haven’t figured it out yet. But crap, I get it, they’ve become an important part of protecting the mail flow. If your clients trust you at all, you can get their permission for a little one-time project like this. My clients were always grateful if I gave them two assurances: (1) it’s important, and (2) they really really don’t want to know anything about the technical details.
A project that needs to become routine: set up backup of Office 365 mailboxes and business data stored in OneDrive. Clients will expect you to have the answer when ransomware takes down business files in some way that keeps OneDrive from handling recovery, or when mailbox data is deleted or destroyed by bad guys.
Insert cliché here

Those are small things. Now it’s time for you to buckle down to the hard stuff. (Or do what I did – give up. Highly recommended but perhaps not practical for everyone.)
Office 365 brings potential but it’s up to you to work with your clients to turn those into solutions.
We buy Office 365 licenses for our clients that deliver a huge number of customer-facing services. Then we set up Outlook mail and maybe OneDrive for Business and we stop. We avert our eyes from the things that aren’t familiar, and our clients do the same because we’ve trained them not to look at anything we don’t tell them about. We’re just procrastinating because learning new stuff is hard. Motivated MSPs can make customers happy by setting up Teams, Booking, Forms, Lists, or Planner, maybe make a few bucks by doing some customer training.
(If you’re an MSP, I strongly recommend that you watch Amy Babinchak’s presentation at a vendor summit last week. She spends an hour on the same theme as these articles but much more oriented to the dollars and cents impact of the changing world on the MSP bottom line, and goes through specific examples of how to monetize Office 365 projects. Thanks to loyal reader Steve Deal for calling my attention to it!)
In the same way, the vast number of security choices in Office 365 create a platform for us to build security solutions.
Microsoft’s Office 365 security options are overwhelming. Our dangerous world requires us to use some of those tools even for the smallest business client. Microsoft calls it a “shared responsibility” model. When you entrust company data and mailboxes to Office 365, Microsoft agrees to take responsibility for keeping the system running (stop snickering, they’re not perfect but reliability is quite high) and for keeping their physical facilities secure.
And that’s it. The rest is up to you. The tools are included with the Office 365 licenses that your clients already own, and far more is available with more expensive licenses that perhaps you should talk your clients into.
All you need to do is thread your way through this kind of security structure.
Yeah, I know, that’s my reaction too. But it’s the proper entry point for small business IT consultants in 2021, and the waters only get deeper from there.
I’m going to throw out a bunch of buzzwords. It will make more sense if you understand that I don’t know what the fuc* I’m talking about. That’s the point. Everything I describe is accessible and your job going forward is to become smart about how to implement these services, how to react to the difficult or unexpected bits, and how to get your clients comfortable with the effects of making things more secure.
More or less, the categories seem to be:
Identity management – various ways to make sure that only licensed users can use devices or access information. There are endless depths to these waters, with role-based access control, just-in-time administrative controls, and more.
Device management – manage and monitor offsite PCs and laptops, mobile devices, virtual machines, embedded devices, and servers, with enforced security policies like “device level pin lock and jailbreak detection,” which are words that absolutely mean things. If you’re wondering what they mean, you could have a good career in IT consulting!
Conditional access – restrict access to corporate email and documents to managed phones or laptops by MAC address or by location-based IP address or by a variety of policies.
It starts with leveraging Azure Active Directory. As near as I can tell, it’s functionally identical if the user logs into a Windows 10 Pro PC with an Office 365 account, or adds an Office 365 account under Settings / Accounts / Work or School. Connecting to Azure AD allows you to use group policy to lock down systems in interesting ways. I guess. I was always intimidated by group policy. I’m sure there are infinite details about implementing cloud-based policies.
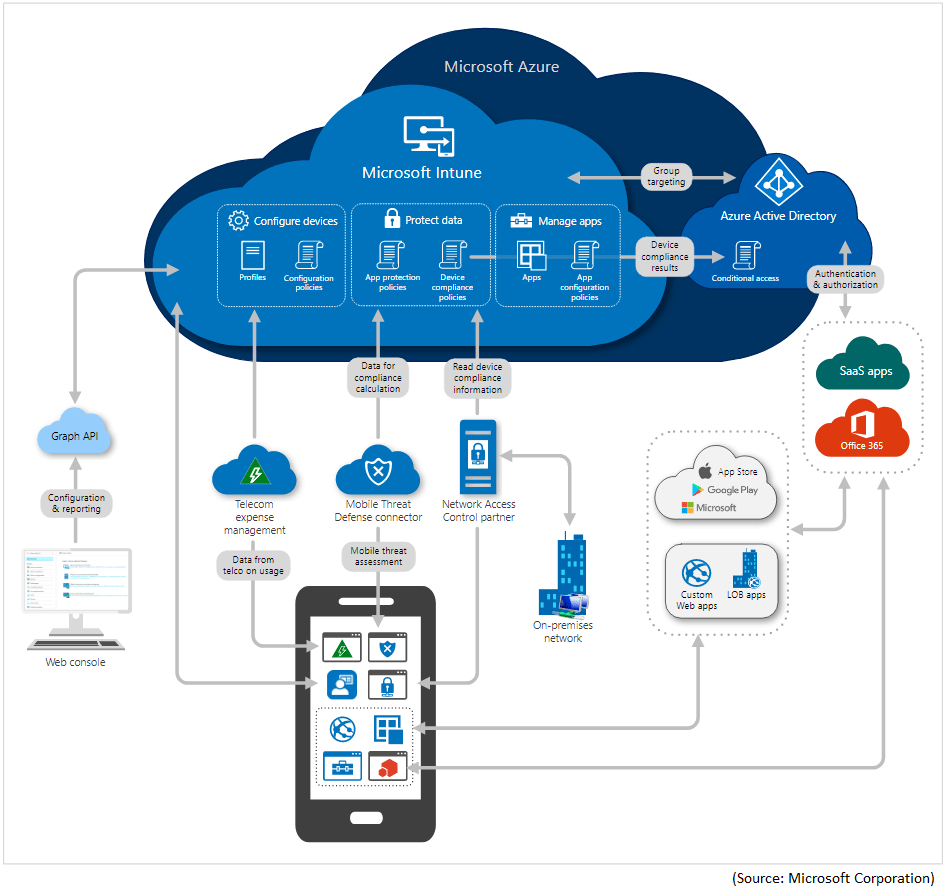
And Azure Active Directory opens up access to Mobile Device Management, included with virtually every Office 365 license.
Once a device is enrolled in MDM, the MDM can enforce compliance with corporate policies, add or remove apps, and more. Additionally, the MDM can report a device’s compliance Azure AD. This enables Azure AD to allow access to corporate resources or applications secured by Azure AD only to devices that comply with policies.
More expensive Office 365 licenses provide access to Endpoint Manager, which includes a smorgasbord of other services, any or all of which might be useful, including Microsoft Intune, Configuration Manager, Desktop Analytics, co-management, and Windows Autopilot. Intune can be used to deploy business apps, Microsoft store apps, and even certificates, Wi-Fi, VPN, and email profiles.
My favorite example of the kind of security enhancement that is possible: you can restrict cut/copy/paste/save as to programs managed by Intune, so that those things just don’t work in other non-managed programs. Pretty amazing, eh?
I’ll bet those services are helpful. I expect to die never knowing anything about the details, because I spent half an hour just now trying to figure out definitively what the names are of the current services and coming up with contradictory, conflicting answers. And that’s just the names! Is Enterprise Mobility & Security a superset that includes Endpoint Manager and Intune? More expensive license? I dunno.
There’s much more. There are various options for logging that can and should be turned on in Office 365. There are enhanced virus, phishing, and malware detection services for Windows and for Office 365 mailboxes, a special version of Windows Defender for servers, and oh so much more.
It’s overwhelming. Not all of it is appropriate for very small businesses – yet. But it is up to the youngsters doing IT consulting today to be familiar with the options for securing business devices and data and to build their MSP business on security. Help desk work and infrastructure projects are no longer enough to pay the bills and more importantly they don’t fill the needs of your clients in a dangerous world.
Educate your clients about the importance of staying secure and avoiding the bad guys. Encourage them to adopt safe practices. And push them to use Office 365 to enforce security by monitoring and managing business data and devices.
Be careful out there!