
Pity the poor forgotten router. You have one in your house or your business. It’s your closest approach to the Internet. The router is the first line of defense that you trust to keep your computers safe. If they do their job, routers do not call attention to themselves and they’re easily overlooked, but they’re crucial to your Internet connection and your security.
Three things you need to know about routers.
• Routers get old. They need to be replaced periodically even if they haven’t completely failed, just like computers.
• Routers should be updated to stay safe, just like computers and phones and tablets. The updates usually improve security or fix a security flaw, and sometimes improve performance. Unlike computers and mobile devices, routers don’t get updated automatically. It’s up to you to check for updates.
• Routers are under attack by bad guys. Your Internet connection might be taken over and your computers might be attacked if you haven’t changed the default password for your router.
I’m not going to give you any specific instructions. There have been 750,000 router models introduced since the beginning of time* and each one has a different story. The best I can do is give you some general ideas about what to look for.
(*This is obviously an exaggerated number used for effect. The real number is less than half that many.)
Let’s get oriented in the world of routers, then I’ll give you some scary security stories to make you feel nervous.
Every network has a router. Your Internet connection enters the building and is handled by a modem from Comcast, AT&T, Sonic, or whoever is your ISP. The connection is then handed to the router, which makes it available to all the devices in the building. The router hands out IP addresses, acts as a firewall to block traffic from outside, and frequently broadcasts the wi-fi network.
It is now becoming common for the modem and router to be a single device supplied by your ISP. If you have a single box from Comcast or AT&T and no other boxes with blinking lights nearby, then it’s your modem AND router AND wi-fi access point.
At one time it was common to have a separate router, like the venerable Linksys WRT54g shown in the picture at the top. We bought consumer routers from Linksys, Netgear, DLink, and many others for many years, and still sometimes today.
Replace your router
The first thing to consider: if your router is more than three years old, there are probably good reasons to replace it. Routers do not last forever and it’s more convenient to replace it before it fails. But there are also constant changes in the world of routers and wi-fi and your router may be falling behind on things that matter. Older routers can be overwhelmed by the speed available from a typical Comcast connection these days. New laptops and phones work best with wireless access points that broadcast the latest generation of signal, 802.11ac; it’s faster and connections are more stable.
ISPs will be less interested in replacing your modem/router, of course, but it still might be useful to ask if you’ve had the same device for many years. Comcast, for example, significantly updated its equipment several years ago to support its faster speeds but I still run into Comcast modem/routers that do not support DOCSIS 3.0 and aren’t delivering the speed that the circuit is supposed to provide. (And Comcast is working on another upgrade to DOCSIS 3.1 for gigabit speeds, which will require more equipment upgrades. The Bay Area is targeted for gigabit deployment in early 2017.)
Update your router
Router manufacturers issue updates for router firmware all the time. The updates might patch vulnerabilities or fix bugs, making it harder for hackers to compromise your network. Nothing will notify you about the updates and they will usually not be installed automatically. Only the very latest equipment – new cloud-connected wi-fi mesh network devices, for example – will receive regular updates. It’s such an important and basic security need that you can expect this to be addressed in the next generation of equipment in the next few years. For now, it’s up to you.
Your router has a control panel that you can access from a web browser. Here’s a bit of networking magic for you:
• Open up a Command Prompt window.
• Type in ipconfig and hit Enter.
Look for the line that says Default Gateway. Write down the number – 192.168.0.1 or 10.0.0.1 or whatever it is.
• Open a web browser and type in http://(gateway_number). Examples: http://192.168.0.1, http://10.0.0.1.
If you’re prompted for a password, you’re probably connecting to your router. The manufacturer name will usually be shown so you can see if it matches the device.
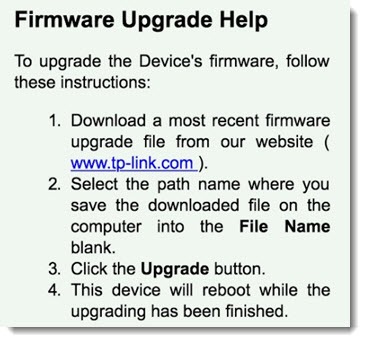
When you log in (see the next section for info about the password), there will likely be a tab for Firmware or Updates. If you’re lucky, it’s an automated process that goes online to download the latest update and install it with a few clicks. If you’re not lucky, the instructions will look something like this – easy if you’re a geek, daunting if you’re a real person.
If you have a modem/router from your ISP, you probably can’t update it and this doesn’t apply.
Change the default router password
There is a login name and password to log into the control panel for the router. You’re at risk if the password hasn’t been changed since the router came out of the box.
This is different than the password for your wi-fi network! Your wi-fi security is important too. You don’t want drive-by hackers to log into your wi-fi and take control of your computers. That would be bad. But it’s different than the password for the router control panel.
If someone has administrative access to your router because they can guess the password, they can completely compromise your network. Your router password is as serious as your computer password or your email password. If someone can log into your router, they can change your wi-fi settings and monitor your network traffic and use your router as a weapon. Bad guys can introduce a subtle attack by changing your DNS server addresses, then send you to malicious fake websites made to look like your bank.
This is an issue because most people never change the default router password. There are online tables of default router passwords for every brand of router. If you can log into your router with the login name admin and password admin, or with the password blank, or with the password password – well, so can anyone else. For years Linksys routers were shipped with a blank user name and the password admin.
Home routers are one of the latest attack vectors for bad guys. A few years ago attackers exploited a vulnerability to change DNS settings for more than 4.5 million routers in Brazil. Another global attack reportedly compromised DNS settings for more than 300,000 home routers. In the worst case attackers might gain access from outside but most routers are set up to prevent that. But that won’t prevent an attack that is launched when you click a malicious link in your web browser, or if a bad guy is close enough to sniff out your network from a nearby building or during a drive-by.
Those attacks won’t work unless the bad guys can guess the router password. Change it from the default!
(If you don’t know the password, it’s a hard problem. Resetting the router has other consequences and might interrupt your wi-fi or disrupt your devices. If you’re not sure of what you’re doing, don’t hold down the reset button without a trusted advisor.)
Router manufacturers are improving security. Most new routers require a new password during setup. Some routers have a unique password printed on the sticker on the bottom, which is good enough security.
Again, routers provided by your ISP are in a different category. Typically you can’t change the login password for a Comcast or AT&T router, but the credentials also do not expose all the deep router settings. It’s still a possible security issue but it’s out of your hands.
A couple of scary examples – always good fun, eh?
Insecure home routers were used to launch denial-of-service attacks against Sony and Microsoft gaming networks, enough to knock them offline over the holidays in 2014.
Carnegie Mellon’s security database CERT issued an advisory this week urging everyone to immediately stop using several models of Netgear routers (R8000, R7000, and R6400) due to a severe security flaw. This one is particularly serious because it doesn’t even require guessing a password; it’s a method for bad guys to seize control of the routers just by getting you to click on a malicious link. Netgear will presumably issue an update for the routers to fix the flaw but has not yet done more than confirm the problem.
One of the largest Internet outages in history happened in October when a denial-of-service attack took much of the Internet offline for millions of people. Mirai is a type of malware that finds devices to infect and gathers them into a botnet that can be centrally controlled. The malware spreads by finding devices with default passwords that can be guessed, which might include home routers. It is particularly focused on cheap “Internet of Things” devices – light bulbs, nursery monitors, cameras, webcams, and more. These are flooding the world and are frequently made with inexpensive chips that have a default password hard-coded into them. The controls are usually not accessible to us and they are frequently not designed to be updated by the manufacturer. That’s the recipe for a botnet army that is still evolving and doing harm.
It’s a scary world out there, and there are a lot of attack vectors to worry about. Don’t let your router bring you down.


Trackbacks/Pingbacks